15. DDS Security Data Visualization with RTI Administration Console¶
RTI Administration Console is compatible with RTI Security Plugins. Configuring security in Administration Console will allow you to visualize and troubleshoot your DDS Secure system. The security configuration is under Preferences > Security. There, you can secure Administration Console’s DomainParticipants by checking the Enable Security for specified Domains checkbox. The security preferences will only apply to the domains listed in the Domain Filter field. Note that a * in this field will apply security to all domains; you can also use patterns like 2,3 or 8,9-12,23.
After setting the Domain Filter to the desired domains where you want to visualize your DDS Secure system, you have to set the security artifacts that Administration Console’s DomainParticipants will use, as shown in Table 15.1, Table 15.2, Table 15.3, Table 15.4.
Note
As a prerequisite for using security in Administration Console, you need to install the RTI Security Plugins. For this, you can follow the instructions in the RTI Security Plugins Installation Guide.
Figure 15.1 is an example of the values to configure Administration Console to work with the “Security::SecureAllowAll” profile of Shapes Demo:
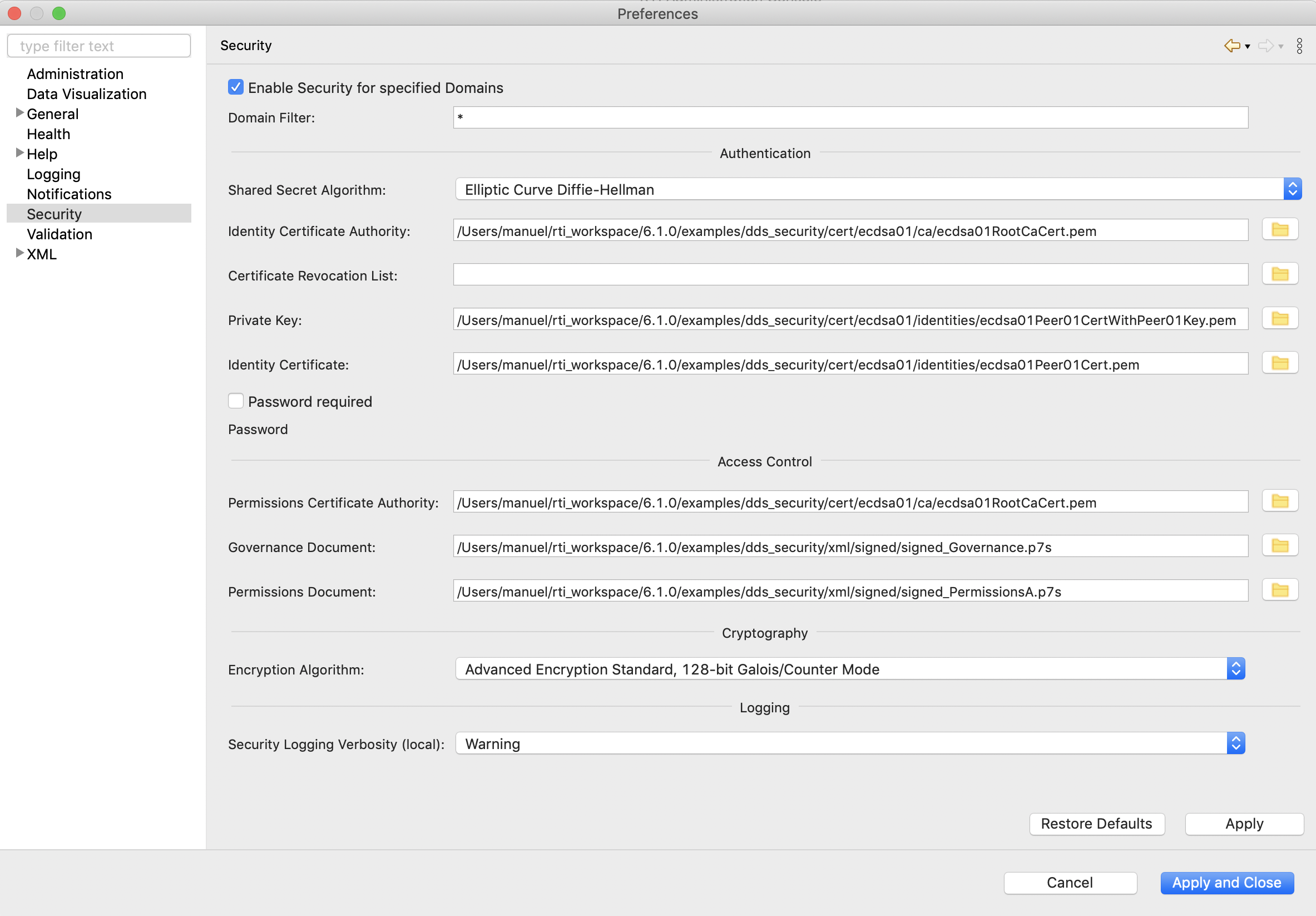
Figure 15.1 Security Panel in Administration Console’s Preferences¶
The following tables describe the purpose of each field.
Note
If you are using Administration Console 5.3.x, make sure to click the Apply button. This is critical because the settings won’t be applied if you just click OK.
Field |
Description |
|---|---|
Shared Secret Algorithm |
Required The algorithm used to establish a shared secret during authentication, as defined by the For details, see Table 4.2. |
Identity Certificate Authority |
Required Provides Administration Console’s DomainParticipants with the Identity CA, as defined by the For details, see Table 4.1. |
Certificate Revocation List |
Optional The Identity CA can maintain a certificate revocation list (CRL) with information about digital certificates that have been revoked before their scheduled expiration date and should no longer be trusted. With this field you can provide the CRL to the Administration Console’s DomainParticipants, as defined by the For details, see Table 4.2. |
Private Key |
Required Provides Administration Console’s DomainParticipants with a Private Key, as defined by the For details, see Table 4.1. |
Identity Certificate |
Required Provides Administration Console’s DomainParticipants with an Identity Certificate, as defined by the For details, see Table 4.1. |
Password |
Only required if the Private Key is encrypted The password used to decrypt the Private Key. This field is interpreted as the Base64 encoding of the symmetric key that will be used to decrypt the Private Key, as defined by the If the password is wrong, Administration Console will fail to create the secure participants and will report multiple errors in the Console Log. |
Field |
Description |
|---|---|
Permissions Certificate Authority |
Required Provides Administration Console’s DomainParticipants with the Permissions CA, as defined by the For details, see Table 5.3. |
Governance Document |
Required Provides Administration Console’s DomainParticipants with the Governance Document, as defined by the For details, see Table 5.3. |
Permissions Document |
Required Provides Administration Console’s DomainParticipants with the Permissions Document, as defined by the For details, see Table 5.3. |
Field |
Description |
|---|---|
Encryption Algorithm |
Required The algorithm that the Sender uses for the encryption transformation, as defined by the For details, see Table 6.8. |
Field |
Description |
|---|---|
Security Logging Verbosity (local) |
Required The logging verbosity level, as defined by the For details, see Table 7.2. |