2.2.9. Step 9: Working with Security Plugins
Admin Console is prepared to work with the Security Plugins, allowing you to subscribe to those topics just like any other Connext entity.
2.2.9.1. Before Using Security Plugins in Admin Console
In order to use security in Admin Console, you must install the Security Plugins; for more information, see Security Preferences.
2.2.9.2. Configuring Security in Admin Console
Admin Console will use the Security configuration specified on the Preferences page, under the Security section. The following image shows the Security Preferences page:
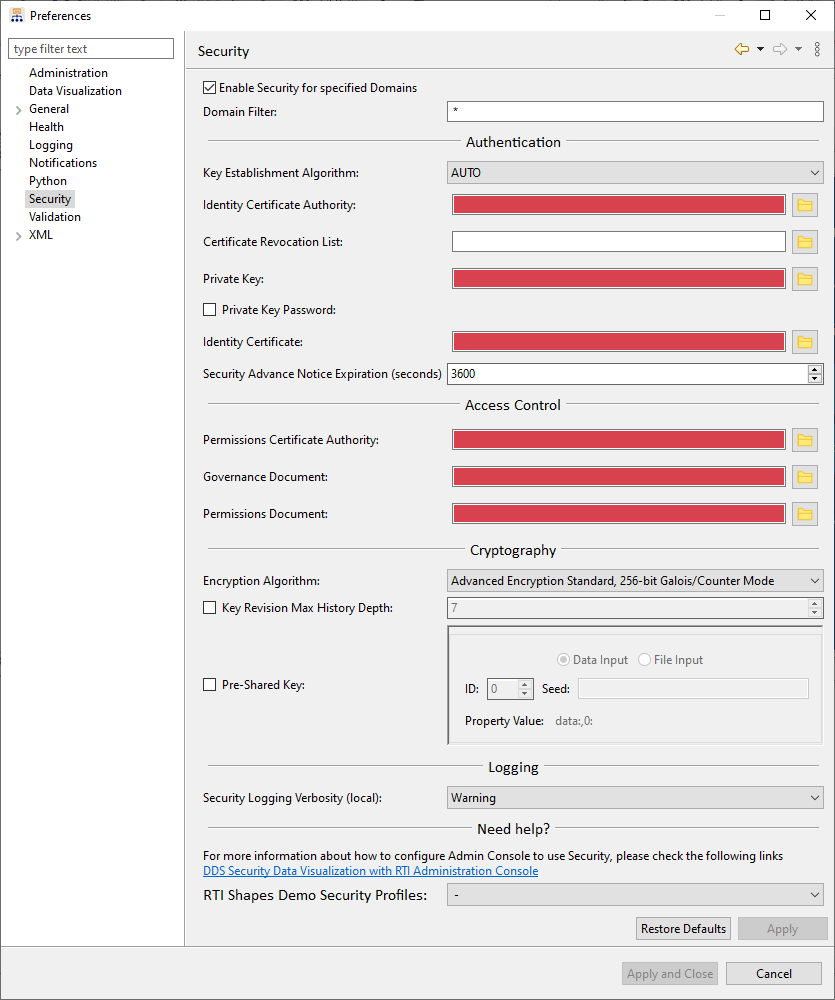
To use the Security Plugins with Admin Console, you must complete the required fields in the Security Preferences dialog. The following list describes all of the available fields:
Enable Security for specified Domains: Select this checkbox to enable security for the domains you designate. By default, security is disabled.
Domain Filter: Provide the domains that need to be secured in Admin Console. Only the domains specified in this field will use security. Enter an asterisk (*) to secure all domains (this is the default value). To secure only specific domains, enter each domain number separated by a comma (for example, “0,1,2”), or specify a range of domains (for example, “0-2”).
Key Establishment Algorithm: Select the cryptographic algorithm to be used to establish a Shared Secret during authentication.
Identity Certificate Authority: Select the Identity CA file for Admin Console’s DomainParticipants.
Certificate Revocation List: (Optional) Select the Certificate Revocation List file to use in Admin Console. This list specifies the digital certificates that have been revoked before their scheduled expiration date and should no longer be trusted.
Private Key: Select the Private Key file that Admin Console’s DomainParticipants must use.
Private Key Password: Select this checkbox if a password is required to decrypt the private key, then enter the password. If the password is wrong, Admin Console will not create the secure participants and will report the issue in the Console log.
Identity Certificate: Select the digital identity certificate file that will authenticate Admin Console’s DomainParticipants.
Security Advance Notice Expiration (seconds): Choose when to be notified that a certificate is about to expire. The default is 3600 seconds.
Permissions Certificate Authority: Select the Permissions CA file to use for authenticated Admin Console DomainParticipants.
Governance Document: Select the Governance Document to use for authenticated Admin Console DomainParticipants.
Permissions Document: Select the Permissions Document to use for authenticated Admin Console DomainParticipants.
Encryption Algorighm: Select the algorithm that the Sender will use for encryption transformation.
Key Revision Max History Depth: (Optional) Select this checkbox to specify the number of key revisions to be used to encode samples. The number must be between 7 and 1000000. If not selected, key revisions are disabled.
Pre-Shared Key: (Optional) Select this checkbox to enable Pre-Shared Key Protection for authenticated Admin Console DomainParticipants. Once selected, the pre-shared key seed fields become available; select the input format, then enter the required property value. For more information about Pre-Shared Key Protection, see the Pre-Shared Key Protection Chapter in the RTI Security Plugins User’s Manual.
Security Logging Verbosity (local): Select your preferred log verbosity level. This selection only applies to the local security logger; it does not affect remote system processes. To view log messages, open the Console log.
RTI Shapes Demo Security Profiles: (Optional) Select the appropriate security profile if securing Shapes Demo participants. For more information, see the RTI Shapes Demo User’s Manual.
Following are some additional notes about using the Security Preferences dialog:
After completing the fields, select Apply; otherwise, your selected preferences will not be saved or applied.
Select Restore Defaults to reset all completed fields.
Each file selected must already exist. If the selected file does not exist, the field background color will change to indicate the file is not valid, and the Apply button will be disabled.
For more information, see DDS Security Data Visualization with RTI Administration Console in the RTI Security Plugins User’s Manual.